If you work(ed) in cybersecurity, especially for a data-heavy or a digital product-led organization, you know how your security devices’ logs and events can get extremely overwhelming. Especially with a decentralized approach or scattered data. SIEM solutions are designed to tackle exactly this. Think of SIEM as a security wingman, turning your attention to patterns and recurring behavior commonly ending up in an actionable preventative remediation. It helps you respond with the most educated visibility over your technology mesh.
What are SIEM solutions?
SIEM – Security Information and Event Management. The term first started appearing in the early 2000s. The need arose when organizations started realizing the importance of centralizing the logs generated by various security devices and systems within their networks. It was primarily used for managing such logs and correlating the data to reach actionable insights within an organization’s cybersecurity measures. However, by time, the solutions evolved to include more sophisticated features like threat-management, incident response and compliance reporting. A typical SIEM solution can aggregate and log data from multiple security devices, systems and solutions like firewalls, intrusion detection systems (IDS), and anti-virus software. Most SIEM solutions today are able to respond to security incidents in real-time, provide compliance reporting and perform in-depth investigations on what’s happening with an organizations’ devices and systems from a cybersecurity perspective. This is an overview of what SIEM solutions are designed to do, check the end of this blog post for a list of the 10 main features a competitive SIEM solution should typically offer.
What are the most competitive SIEM solutions?
While the list may change over time, some vendors offer industry standard SIEM solutions, some of this organizations are, but aren’t only those, but it is MHE’s team choice balancing between features, investment and ease of deployment and use:
- Crowdstrike‘s LogScale
- Palo Alto – Cortex XSIAM
- Elastic
- NetWitness Platform
- Alienvault USM
- Fortinet – FortiSIEM
- ManageEngine
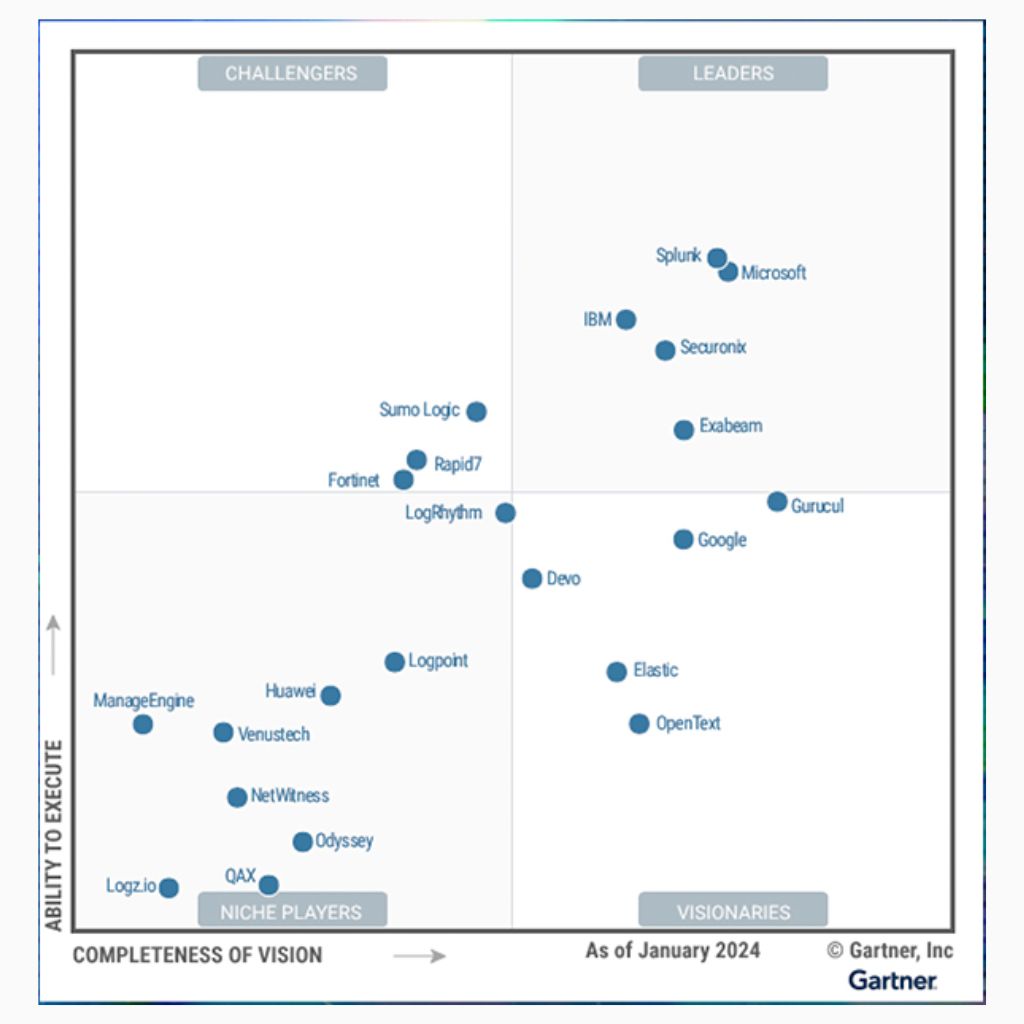
Obviously, it is not a binary choice, the selection of an adequate SIEM solution depends on multiple factors, between budget, the complexity of the IT infrastructure, and the specific security needs. However, the good news is that some providers do not require proprietary technology for the SIEM solution to deliver the needed function. Get in touch with MHE’s team to discuss your technology needs and find the most suitable SIEM solution for your organization’s size and requirements.
Is SIEM solution a pricey investment?
Competitive, enterprise-grade SIEM solutions can be expensive to deploy as they require some investment in hardware, software, maintenance, and support. But the good news is that smaller organizations can deploy open-source alternatives that might come with their limitations, but then again, it depends on the use-case and the type of organization. Before deciding, make sure your appointed cybersecurity professional conducts thorough research on the available solutions to find the right balance between investment and fulfilment.
But you don’t have to burden the budget …
MHE‘s team is well seasoned in matching needs and budgets. One of the most cost-effective SIEM solution implementations is a combination of Elastic + Wazuh. Elastic stack is deployed for log analysis and application performance monitoring. This enables real-time visibility into IT environments, detects anomalies, and aids with compliance reporting. Elastic’s tools are adapted for SIEM observability, and business intelligence, ensuring faster decision making and reduced operational cost. Fill this form if you’re interested in a POC.
Do all organizations need a SIEM solution?
As a cybersecurity-centric service provider, we will definitely say yes. However, a more objective answer would be, not always. Why? Because if your logs are limited and manageable, then you could be on the safer side, especially if you do not collect or store a lot of sensitive data. However, it is worth considering at a later stage. Especially with the growth of both the number and the intelligence of cybercriminals and their tools. Behavior-based attacks are becoming trendier and the age of referring to an attack database and securing your assets accordingly is quickly fading away. Typically, the organizations that require SIEM solutions (some of which need to comply to nation-wide policies and regulations) are:
- Government agencies
- Healthcare organizations
- Oil and gas organizations
- Large enterprises
- Financial institutions
The reasons for government agencies are obvious. Healthcare and financial institutions store personal data that are considered some of the most sensitive and most sought-after data by cybercriminals, that’s why in some countries such institutions are required by law to deploy SIEM solutions.
Here is why SIEM solutions help such organizations protect their data on a much larger scale:
- Log Collection and Aggregation: The ability to collect and centralize log data from various sources within an organization’s network.
- Real-Time Event Monitoring and Alerting: The ability to monitor and analyze log data in real-time to detect and respond to potential security threats.
- Threat Detection and Analysis: The ability to use machine learning and behavioral analysis algorithms to identify and prioritize security incidents and threats.
- Compliance and Regulatory Reporting: The ability to generate reports that meet various compliance and regulatory requirements, such as PCI DSS, HIPAA, and others.
- Incident Response and Forensics: The ability to quickly respond to security incidents and perform in-depth investigations to determine the root cause of the incident and take remediation actions.
- Integration with Other Security Tools: The ability to integrate with other security tools and solutions, such as firewalls, intrusion detection systems (IDS), and anti-virus software.
- Dashboards and Reporting: The ability to view and analyze log data and security incidents through customizable dashboards and reports.
- Data Retention and Archiving: The ability to store log data and security incidents for a specified period, typically several years, for historical analysis and compliance purposes.
- User Management and Access Control: The ability to manage and control access to the SIEM solution by different users within an organization, such as security administrators and security analysts.
- Mobile Access: The ability to access the SIEM solution from mobile devices, such as smartphones and tablets, for remote monitoring and incident response.
Is there a difference between SIEM and XDR solutions?
This might not be a straight-forward answer, but in short, Extended Detection and Response (XDR) solutions are an extension of SIEM solutions. But there are some differences in the way they operate and respond to threats. Stay tuned for our XDR vs. SIEM blog next week to have a more in-depth understanding of the core differences between both solutions!






