Ransomware has not been the biggest concern for cybersecurity professionals in 2023, albeit being a priority still. According to the 2023 SonicWall Cyber Threat Report, Less Ransomware incidents have actually been reported in 2022 compared to 2021. Yet, a recent data leak on the dark web has signaled a novel ransomware attack that is here to make a name for itself. The demanded ransom for the recorded cases so far is $10,000, which is not the largest sum in similar attacks, but Dark Power managed to claim 10 victims in its first month only!
About Dark Power Ransomware:
What we know so far, is that Dark Power’s payload is written in Nim, a cross-platform programming language that has been gaining popularity among malware authors recently. The edge that Nim has over other languages are speed related, which makes it a suitable choice for performance-critical applications. According to this Trellix’s blog post, no specific sector or geographic area is targeted by the gang behind Dark Power, but they see a rather opportunistic gang trying to make money from their victims. Trellix also claims that Dark Power’s website is filled with victim naming and shaming, but the victims are non-paying.
| Filename | ef.exe |
| MD5 | df134a54ae5dca7963e49d97dd104660 |
| SHA-1 | 9bddcce91756469051f2385ef36ba8171d99686d |
| SHA-256 | 11ddebd9b22a3a21be11908feda0ea1e1aa97bc67b2dfefe766fcea467367394 |
| File size | 1323422 bytes (1.3 MB) |
| Compile date | 2023-01-29 02:01:33 |
| Compiler | Nim MINGW x64 |
Unfortunately, there is very little information available on the infection point, and how the victim executes the .exe, but it could be a phishing email or any other means.
Here’s how Dark Power gains hold of your data
Upon execution the ransomware creates a randomized 64-character long ASCII string to initialize the file encryption algorithm with a unique key for each victim.
1. Encryption Key initialization:
When it begins, the ransomware generates a 64-character lowercase ASCII string randomly. This string initializes the encryption algorithm at a later stage, as shown in the figure. Because of the randomization, the key is different every time the malware runs, making it unique on each infected device. This makes it challenging to create a decryption tool that works on all machines. The Nimcrypto library is utilized in the sample to perform cryptographic functions, using the AES CRT algorithm.
2. Encrypting the binary string:
The ransomware employs encryption to obscure its strings, potentially impeding defenders from creating a generic detection rule. The encrypted strings exist within the binary in base64 encoded format. Subsequent to decoding the ciphertext string, a fixed key – namely the SHA-256 hash of a hardcoded string – is utilized for its decryption. Furthermore, the binary comprises the initialization vector (IV), albeit each decryption attempt uses a distinct IV.
The aforementioned disassembled instructions serve the purpose of decrypting a string, which ultimately yields “.darkpower” as output. The IV is loaded into “rdx”, while “rax” serves as a storage for the base64 encoded and encrypted string. Invoking the function call to “decrypt_AES_CTR” decrypts the specified string.
To facilitate the malware’s analysis, decryption of all encrypted strings is possible, as depicted in the accompanying image. By doing so, an analyst can better comprehend the ransomware’s internal mechanisms.
3. Taking hold of key Services:
The Dark Power ransomware directs its focus towards specific services on the victim’s device. These services include veeam, memtas, sql, mssql, backup, vss, sophos, svc$, and mepocs, which the malware halts. This obstructs the victim’s ability to recover their files, as the stoppage of these services could free files (such as databases), making them susceptible to encryption by the ransomware. In addition, the ransomware brings to a halt the Volume Shadow Copy Service (VSS), as this is commonly done by malware. The VSS stores shadow copies of files.
Also, various other backup and anti-malware services are terminated. The overarching aim is to increase the likelihood of the victim giving in to the ransomware’s demand for payment. If the malware detects any services or processes that match the predetermined list, it will print “[YES] in killing (service name)” to the console, as shown in the figure below.
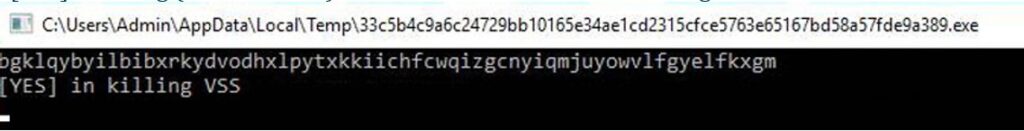
Stopping Key Console Message
4. Terminating Processes:
In the same manner as taking hold of key services and stopping them, processes in the infected device that block files (such as those office-related ones) are often also terminated. Dark Power queries WMI (Windows Management Instrumentation) named winmgmts: & {impersonationLevel=impersonate}!.\root\cimv2” with the query “select * from win32_process”. The previous compiles a list of all the running processes and when it finds processes that match a predefined list similar to taskmgr.exe, firefox.exe, or office-related ones like powerpnt.exe or visio.exe and terminates them. Dark power also targets processes known to be linked with database activity such as sql.exe, oracle.exe or dbsnmp.exe to make sure the offensive encryption takes place on all known database files. This ensures that the malicious script is able to control all related files and encrypt them without the risk of running into locked files.
5. File and folder exclusion:
For the victim to be able to read the ransom note, the system needs to be left operational. After Dark Power takes hold of all files, folders and keys, it runs an additional filter that excludes system files, folders and extensions that are crucial for the operating system to stay up. Some of the excluded system files extensions are (.lib, .theme, .dll, .bin, .ocx, .msi, .mpa, .cab and the likes -overall around 57 extensions-) along with some other files (readme.pdf, autorun.inf, bootfont.bun, ntuser.dat, ntldr, ntuser.dat.log … etc.) and key folders (program files, appdata, windows.old, intel, windows, application data, program files, perflogs, $windows ~bt, boot, google)
5. Clearing logs and consoles:
As is the custom with most ransomware offenders, the script is coded to erase all the logs and console data to cover its tracks. The ransomware sleeps for 30 seconds after killing the services, and then runs the /c cls Windows command to clear the console. And to clear the system log, the WMI query “Select * from Win32_NTEventLogFile” and “ClearEventLog()”. This concludes the steps before spreading the ransom note and excryption process.
6. Displaying the ransom note:
On every folder hijacked by the attacker, a ransom note will be placed for the victim to find. And unlike most ransomware where notes are scared in a notepad file or plain-text. The ransom note of Dark Power is a .pdf file using Adobe Illustrator 26.0.
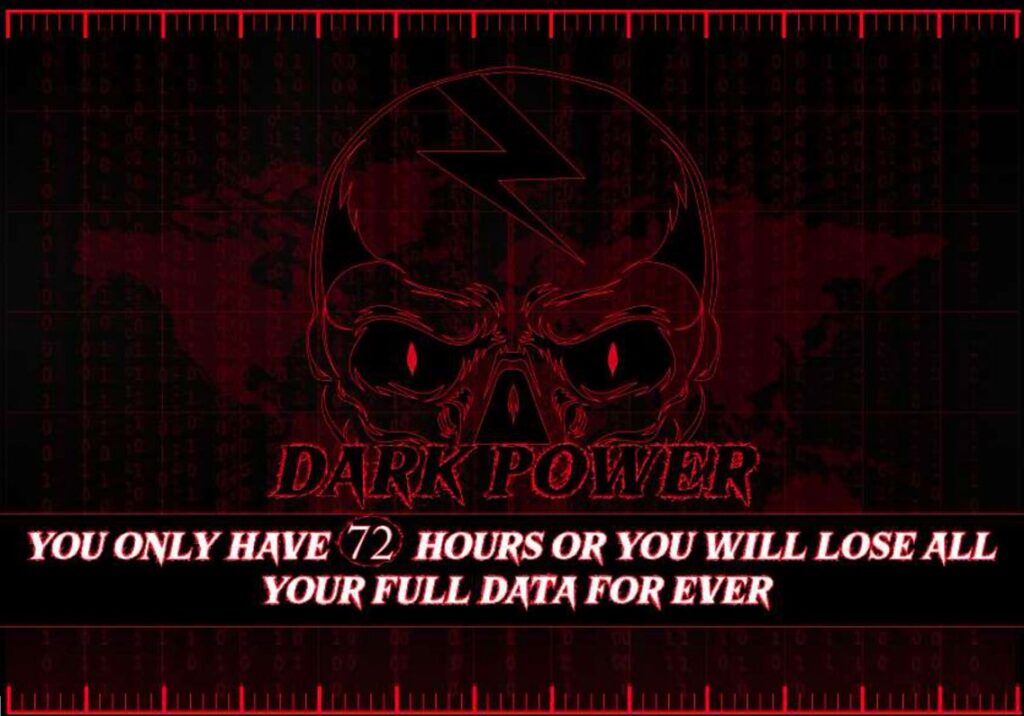
Dark Power Ransom Note screenshot.
The attacker demands $10,000 USD in ransom, transferred to a Monero blockchain wallet, while redirecting the victims to a Tor website showcasing the claimed victims of the attack. The victims also get a chance to chat with the attackers using a qTox ID (For Anonymized messaging) on the same Tor site.
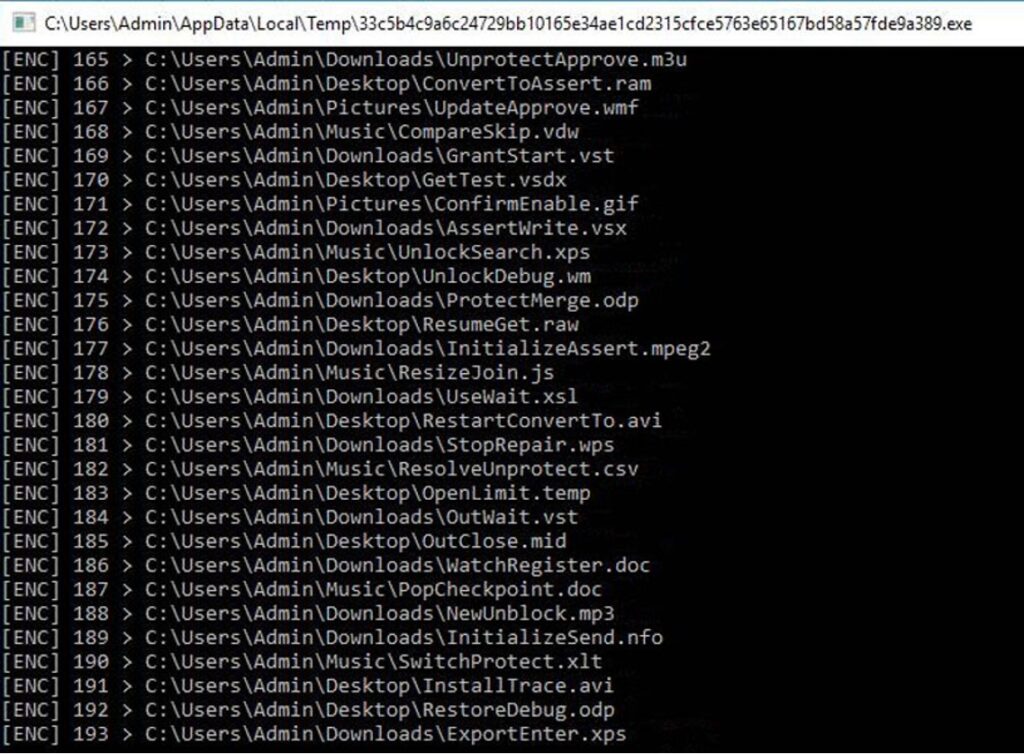
6. Encrypting the remaining files:
After the vital processes and files are excluded, the encryption of the remaining files is initiated. Using the AES (CRT mode), the encrypted files are printed on screen, along with their extensions and a counter. After a full encryption of the file contents, the encrypted file extensions are renamed to “.dark_power”
7. Threat intelligence:
The Dark Power group is one of many active ransomware gangs. Most gangs, like Dark Power, extort their victims twice, the first time upon holding and encrypting the data, and a second when the ransom is not paid, the stolen data is published online.
While this particular ransomware doesn’t upload the data in a programmatic manner, it is assumed that the exfiltrated data is uploaded manually post infection. From the exposed victims so far, it is not likely that the Dark Power gang has a specific target, the victims claimed so far are in Algeria, Czech Republic, Egypt, France, Israel, Peru, Turkey and the USA, with the victims operating in different sectors like education, IT, healthcare, manufacturing and food production.
While paying the ransom may get you your files back, the decryption does not always ensure restoring the files to their original state. Some files get corrupted during the encryption/decryption process. Furthermore, it is not advised to engage with ransomware gangs as this only encourages such malicious acts of crime.
Cyber attackers and criminals will keep growing through learning new languages (like Nim, Golang, and Rust) the cost of continuous knowledge spreading and education among the defending side might be higher, but it is vital and needed. Some Managed Services Providers like MHE provide ransomware protection and dark-web monitoring as a service for interested organizations, but you should also consider Cybersecurity Awareness programs for your team to help them stay safe in the cyber world, If you’d like to take a birds-eye look on your cybersecurity landscape, check out this insightful post about the 7 layers of cybersecurity, it will help you easily spot the vulnerabilities in your current posture, and where it is best to start bridging the security gaps.
