The team at McAfee Research Labs has been getting busy analyzing a new malware dubbed ‘Goldoson’. 60 legitimate applications on Google’s Play Store that collectively have over 100 million downloads were affected. The malicious script occurred in a shared public library file that is used by the developers of the 60 applications, not knowing that it is a compromised library file.
Some of the applications infected with Goldoson:
- L.POINT with L.PAY – 10 million downloads
- Swipe Brick Breaker – 10 million downloads
- Money Manager Expense & Budget – 10 million downloads
- GOM Player – 5 million downloads
- LIVE Score, Real-Time Score – 5 million downloads
- Pikicast – 5 million downloads
- Compass 9: Smart Compass – 1 million downloads
- GOM Audio – Music, Sync lyrics – 1 million downloads
- LOTTE WORLD Magicpass – 1 million downloads
- Bounce Brick Breaker – 1 million downloads
- Infinite Slice – 1 million downloads
- SomNote – Beautiful note app – 1 million downloads
- Korea Subway Info: Metroid – 1 million downloads
The attack gains access to some important user device data including installed apps, WiFi & bluetooth-connected devices, and the device’s GPS location. The device could also be enrolled in a fraud botnet targeting ad clicks without user’s consent.
Adversarial Technique:
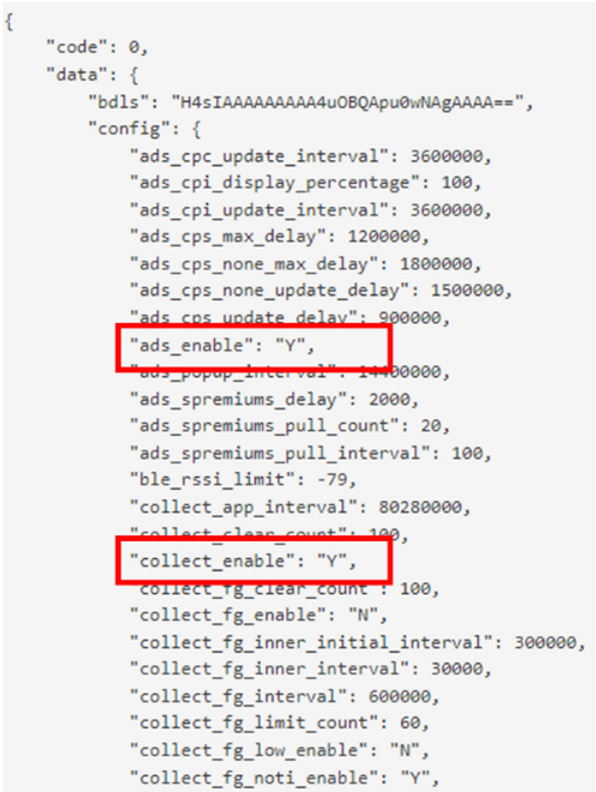
Goldoson Configuration (McAfee)
- Once the victim opens one of the compromised applications, the library file registers the device and its configuration onto an obfuscated-domain remote server.
- The configuration sets the parameters to how often both the exfiltration and the ad-clicking functions should run.
- The data collection (exfiltration) function runs every two-days by default, sending a list of installed apps, geo-location history, and MAC addresses of the devices connected via WiFi or Bluetooth to a C2 server (below you will find the JSON exfiltration request)
The extent of data gathering by an infected app is dependent on the access granted during its installation and the Android operating system version in use. Although Android 11 and newer versions have improved protection against unauthorized data collection, McAfee’s investigation showed that Goldoson had enough access to obtain sensitive data in 10% of the apps, even in recent Android OS versions. The ad-clicking function operates by loading HTML code and inserting it into a custom hidden WebView. The WebView is then used to visit multiple URLs and generate ad revenue, without the victim noticing any such activity on their device.
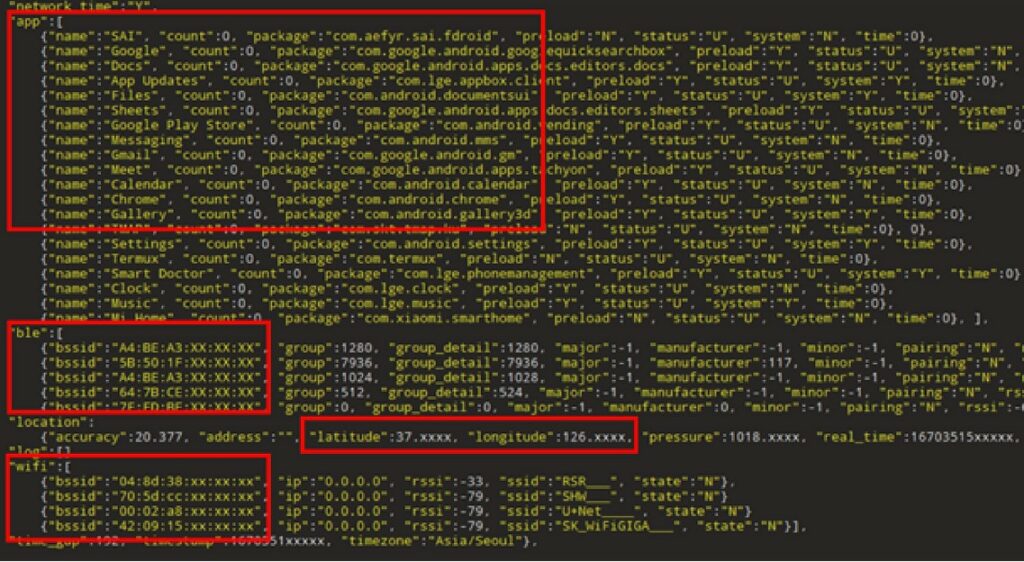
JSON data exfiltration request by McAfee
The Ad-clicking activity is not yet confirmed to invoke further downloads, but is revenue-generating for the attacker from the looks of the links in the “Response” tab in the network activity.

Goldson’s Ad-Clicking activity (McAfee)
It is worth mentioning that McAfee is a Google App Defense Alliance member. The alliance helps keep Google Play as clean as possible from Malware, Adware and threats in general. Once the above vulnerability was spotted, the findings were forwarded to Google, consequently alerting the developers of the infected applications.
While many developers managed to clean their apps by getting rid of the offending library, some of the developers failed to get back to google with a reply within the designated time to action. Accordingly, the late-responders had their applications removed from Google for non-compliance with the store’s security policy.
Those who had earlier installed versions of the infected applications can remediate this by redownloading the latest updated version with the library removed.
Sources:
Android malware infiltrates 60 Google Play apps with 100M installs (bleepingcomputer.com)
