Endpoint Protection is a front and center cybersecurity priority for today’s data-driven organizations. While the amount of data on each individual device might not be valuable on its own and might not be considered a massive loss if compromised, it still signals vulnerability towards smarter data breaches that could have a heavier impact on your organization’s brand value.
What is MITRE Engenuity ATT&CK Framework?
ATT&CK Framework
The MITRE Engenuity ATT&CK (Adverserial Tactics, Techniques & Common Knowledge) Evaluation is among the world’s most respected third-party security tests. It provides organizations with a critical and objective assessment of product performance. The results indicate a solution’s ability to provide security analysts a quick, clear picture of how an attack unfolded. Participating vendors are measure on their ability to detect and address real-world threats through the language and structure of the ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) Framework. The 2022 Enterprise ATT&CK Evaluation emulates the real attack methods of Wizard Spider and Sandworm, two APT threat groups that conduct ransomware campaigns for financial gain and data destruction. Traditional sandboxing technology,” said SonicWall SVP and Chief Technology Officer John Gmuender. “As cyberattacks continue to strengthen and escalate, so must technology and the creative thinking of researchers who work around the clock to ensure that organizations in all industries can advance their reliance on the digital and connected world.”
Sentinel One scored perfect results in the 2022 edition:
- 100% Protection, 9 of 9 MITRE ATT&CK Tests.
- 100% Detection, 19 of 19 Attack Steps spotted.
- 100% Real-time, 0 Delays.
- 99% Visibility, 108 of 109 Attack Sub-Steps.
- 99% Highest Analytic Coverage 108 of 109 Detections.
What Do the Results Mean for My Organization?
SentinelOne’s performance demonstrates how Capture Client is uniquely positioned to drive business value and help organizations excel across major KPIs

Why Capture Client powered by SentinelOne?
Capture Client with SentinelOne’s superior visibility, actionable context, the ability to defeat adversaries in real-time and out-of-box efficacy sets us apart from every other vendor in the market.
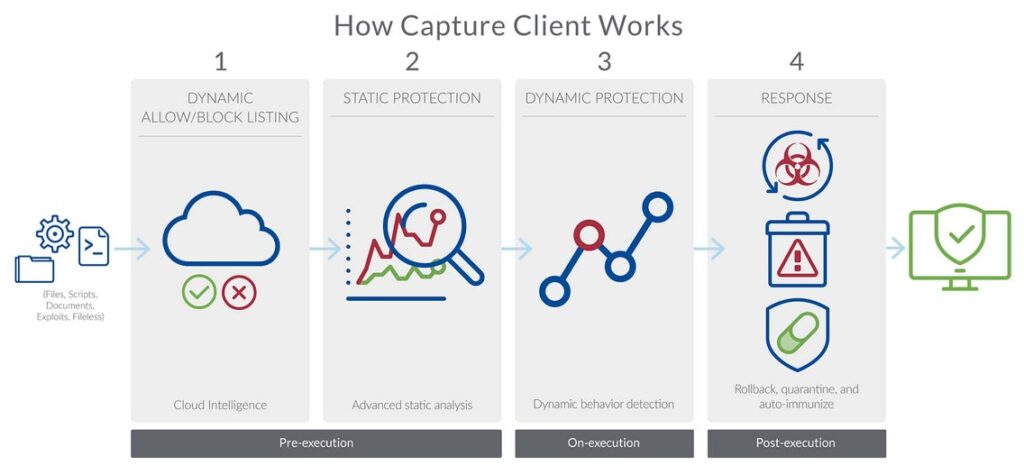
How Capture Client Advanced with SentinelOne Rollback Works
Capture Client Advanced monitors all activities and actions on the protected devices, maintaining a full storyline of behavioral data. Behavioral AI modules analyze all activities as they happen, providing real-time classification of potentially malicious actions. Capture Client Advanced is aware of every operation on the device. Therefore, if it reaches a verdict of malicious, it can restore the device to the pre-malicious recovered state, without impacting benign activities on the device. Capture Client Advanced recovers registry keys (often used by malware for persistence), scheduled tasks, and other internal operating system functions. To do this, the Rollback feature utilizes Microsoft Windows Volume Shadow Copy technology (VSS) instead of relying on limited caches of files saved for an emergency. This technological integration is natively built into all enterprise-grade Microsoft operating systems. At the same time, Capture Client Advanced protects the VSS to ensure no malicious activity can interfere with the ability to rollback their impact. In other words, it creates tamper-proof shadow copies in the event malware does slip through.
How SonicWall Capture Client Powered By SentinelOne Works
Rollback Example:
Let’s look at potential situations where Capture Client Advanced with Rollback could be used. In the first scenario, an employee uses a standard device. The device has Capture Client Advanced configured in an alert-only policy (no protection). The user visits website with a malicious payload, and unknowingly downloads a document with malicious code to the device. Capture Client Advanced monitors this and all other operations. When the user opens the file, they trigger the malicious
code. It copies files and changes files, registry keys, and scheduled tasks on the endpoint. Capture Client Advanced records all of these activities, along with every operation related to it. Alternately, in a second scenario, the device has Capture Client Advanced configured in a protect policy, it would immediately block this attack using static AI scanning and behavioral AI models, thereby successfully mitigating the detected actions and process flow. This capability is unique to SentinelOne technology used by Capture Client Advanced. In this example, Rollback restores the device. The Rollback functionality traverses the entire storyline, locating every file that was affected during the infection. Then, Capture Client Advanced restores each file from the VSS storage to its state before the infection. Capture Client Advanced restores the device to its perfectionate by undoing the actions in the storyline. The user continues working without loss of data. No downtime, no data loss, and a holistic approach to solving the ransomware problem.
If you’re interested in SonicWall’s Capture Client EDR solution, get in touch with MHE now.
