Digital transformation is accelerating the pace at which organizations are switching to online-facing applications. Whether the server is local, remote or cloud-based, cybercriminals are finding it easier than ever to attack many businesses online now. If you are the owner of a business that accepts data transactions online via form fills, file uploads or payment gateways, a Web-Application Firewall is definitely a must-have within your technology portfolio. In this blog post we’ll take a quick look on the basic functions of a WAF solution, and who any online business needs it now more than ever.
What is WAF?
A web-application firewall plays a critical role in the security of any organization with public-facing web applications. It protects your online applications by targeting Hyper Text Transfer Protocol traffic (HTTP) threats through and/or data monitoring and filtering which is why WAF
“A web-application firewall plays a critical role in the security of any organization with public-facing web applications.”
By implementing a WAF solution, your online applications are protected from malicious attacks such as DDoS (Distributed Denial of Service), XSS (Cross-site scripting), SQL Injection, Bot and API attacks. Making sure that you do not face any unpleasant consequences like data breaches or service failure, by protecting the application layer and providing security to the 7th layer of the TCP/IP networks’ OSI Model.
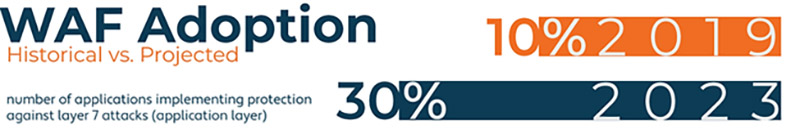
A research anticipates that by 2023, at least 30% of web applications globally will have WAF. Compared to 2019, when only 10% of web applications used WAF in one of its formats. Which brings us to this next question;
What are the types WAF?
There are three types of environments that typically include web-facing applications:
- A Network – Based web application: The advantage of a network-based WAF is throughput and performance. Which is why it is typically used by large enterprises with hundreds of thousands of data transactions done on a daily basis.
- A Host – based web application: Is installed on a VM (virtual machine). The core advantage of a host-based WAF is deployment flexibility. When we compare WAF solutions for host-based applications with their hardware counterparts, we find that the earlier is more budget friendly than the latter, the deployment is mostly virtual also, so the hassle of physical shipping and installation completely vanishes. Organizations with host-based web and application servers, such as data centers and hosting providers prefer the “virtual appliance” format than the hardware format.
- Cloud – based web application: While the last two formats would fit most of the architectures, a newer generation of WAF that is provided and managed directly by a service provider in the form of SaaS (software-as-a-service) promises new benchmarks for ease of deployment. The major advantage is effortlessness, as the user doesn’t need to install any software locally.
We’re not going to go too deep into the details, but if you’re interested in a deeper dive, you can check out this blog post. But now that we know what WAF is and who needs it; let’s take a quick look on why most modern businesses with operating models that depend heavily on online data transactions will sooner or later need to deploy a WAF solution.
95% of web-applications were hacking vectors for cyber-attackers in 2021
Why the need for WAF?
The cybersecurity threats on web-facing applications are evolving at an exponential rate. Cybercriminals’ hacking tools are becoming more sophisticated. The motivation is usually to engage in unlawful acts as blackmailing and illegal trading of such data. In short, WAF protects against different types of threats which are nowadays automated like Advanced Bot Attacks, which mainly target web-applications and is perceived as one of the top App Security challenges . In the same study, Barracuda Networks concludes that 95% of web-applications were hacking vectors in 2021!
The rising trend of digital transformation is also giving cybercriminals a priceless bounty to go after, especially that a vast majority of entrepreneurs and decision makers pay a lot of attention to the value of the data they possess, but pay little attention to to their liability towards such data. In fact, almost 72% of IT leaders admitted their organizations have been attacked at least once in the past year alone!
What are we up against?
The Open Web Application Security Project (OWASP for short) is a nonprofit foundation that works to improve the security of software. In their quest to focus the community’s attention to the common enemy, OWASP publishes a periodic report on the top software vulnerabilities, and providing a standard -albeit optional- for developers and DevSecOps to use for benchmarking their applications’ security status.
MHE could help you identify the best scenario to protect your online-facing, or web-applications from threats that could potentially harm your organization’s progress. With a free assessment, you will have an overview over your application’s vulnerabilities, and a roadmap on how to protect your If you feel like having a conversation about Web Application Firewalls, you can check our team’s online calendar, and book a call to answer any questions you might
have, no strings attached.
